{tocify} $title={Table of Contents}
Create a simple http triggered logic app
which will get triggered upon receiving http request and sends back whatever it receives as response by prefixing it with "Following is what you sent:-" .
Read - Getting Started with Azure API Management - Fundamentals
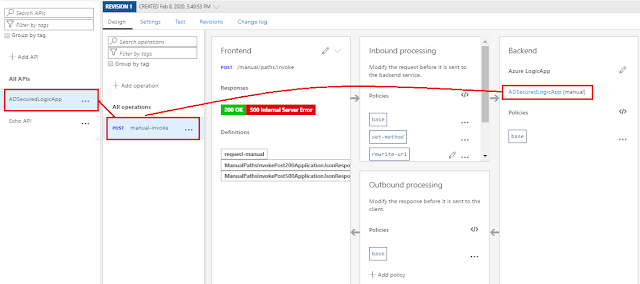
Now import Logic App by going to API -->Add API --> Logic App
Below is how it should look, an API is created ADSecuredLogicApp having an operation manual-invoke and backend set to the imported logic app url
Validate by - As we are going to check header , set this to header.
Header name - name of header to be validated, set this to Authorization
Failed validation HTTP code - what HTTP error code you want to return when validation fails, set this to 401
Failed validation error message - what error messages you want to return when validation fails
Required signed tokens? - All Azure tokens are already digitally signed so it has no effect but,set it to Yes.
Require scheme - Which authorization scheme you want, set it to Bearer
Audiences - Against whom the token is to be validated, enter the Application ID of the AD app created in step 1
Open ID URLs - This is Authority which APIM will call internally to validate the received token, either of the below can be used
https://login.windows.net/<tenant_name>.onmicrosoft.com/.well-known/openid-configuration
https://login.windows.net/<tenant_id>/.well-known/openid-configuration
As logic app does not understands Authorization header , we need to remove it before forwarding request to Logic App and that can be done by using Set headers policy
Read - The request has both SAS authentication scheme and 'Bearer' authorization scheme. Only one scheme should be used
Configure Set Header Policy
Policies should look like
And in code view
That's it, the Logic App is now secured with Azure Active Directory by using Azure APIM. So if someone has to access the logic App it has to present Access token and make a call to the Url set in APIM
For testing it , have used another Logic App which will make call with access token to new URL.We need now the URL of API created in APIM (whose backend is Logic App), we can get it from Test tab as below.
Below is http based Logic app which makes call to API url and collects the response and sends back
Have covered detailed steps in following post for details - Calling Active Directory Secured Function App from Logic Apps
Using postman, did sent a request to above callerlogicapp and received a response
Introduction
In previous post - Securing Function App with Azure Active Directory authentication we saw how function app can be secured with Azure active directory and how to make call to it. And it was done by creating an AD App which acted as Audience and and was responsible for validating the access token.
And as Azure Function App supports AD authentication, the Audience app can be assigned/linked to it.
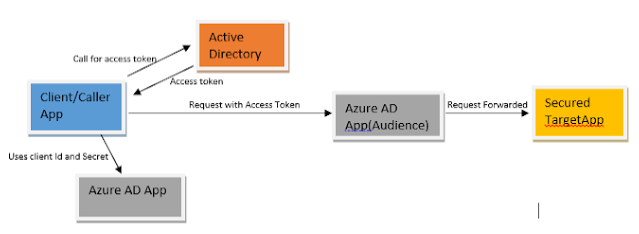
So how do we use Azure Active Directory to secure Logic App? It can be done with the help of Azure APIM, where we ask it to do the task of validating the token and rest all remains same.
And as Azure Function App supports AD authentication, the Audience app can be assigned/linked to it.
So the first thought would be that same can be done with Logic App, why this post? - Ideally it should be but it is not because not all Azure services support Azure AD authentication and Logic App is one of them. Microsoft has a plan for adding/integrating support for all All Azure services, but it will take some time.
So how do we use Azure Active Directory to secure Logic App? It can be done with the help of Azure APIM, where we ask it to do the task of validating the token and rest all remains same.
i.e. whoever has to access the logic app needs to get a access token from Azure AD Tenant(Authority) in which Logic app resides and present it along with the request which will be validated by Azure APIM (using AD application's info which is created for logic App) and only after validation is done request is forwarded to Logic app.
Thus Logic App gives away the task of security check to Azure APIM (no code required in logic App).
Steps to secure Logic App using Azure AD
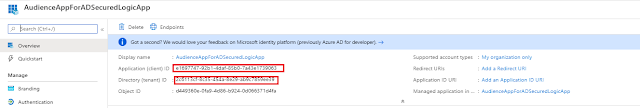
Register an Application with Active directory (AudienceAppForADSecuredLogicApp - Audience)
- Sign in to your Azure Account through the Azure portal.
- Select Azure Active Directory.
- Select App registrations.
- Select New registration.
- Name the application. Select a supported account type, which determines who can use the application.
Below is what you should see, make note of Application(Client) ID -- this will be used as Audience by caller app when access is requested.
Create Logic App
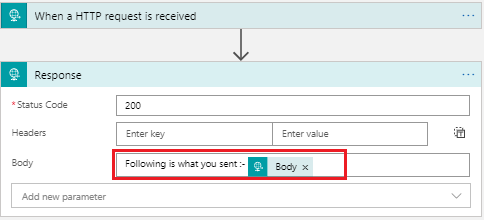
Create a simple http triggered logic app
which will get triggered upon receiving http request and sends back whatever it receives as response by prefixing it with "Following is what you sent:-" .
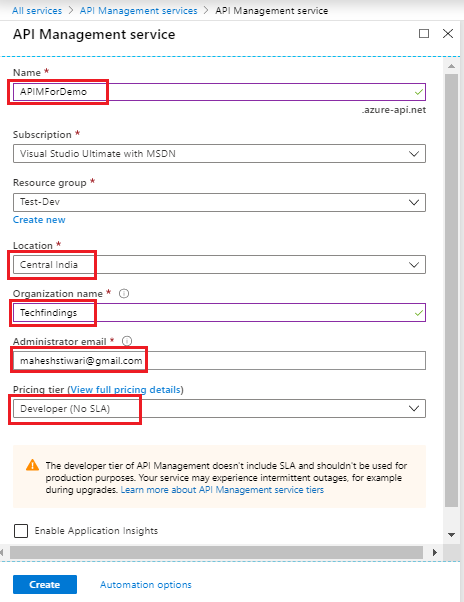
Create APIM Instance and Import Logic App
Read - Getting Started with Azure API Management - Fundamentals
Below is how it should look, an API is created ADSecuredLogicApp having an operation manual-invoke and backend set to the imported logic app url
Note: When you add logic app as an API,you already are adding a security layer, where your logic app url gets hidden and a new url is created which is shared .
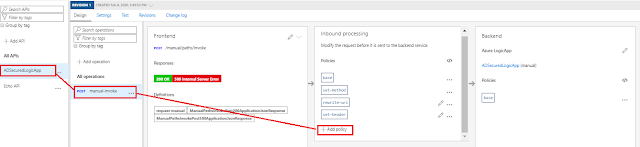
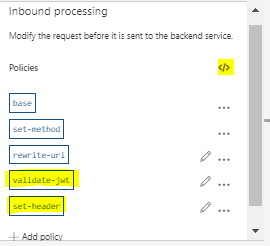
The base is ready, now we need to add the Policy in Inbound Processing Section which will validate the token
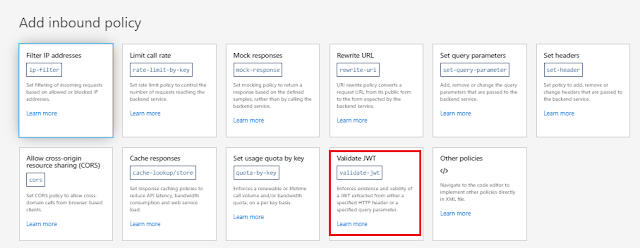
Select Validate JWT
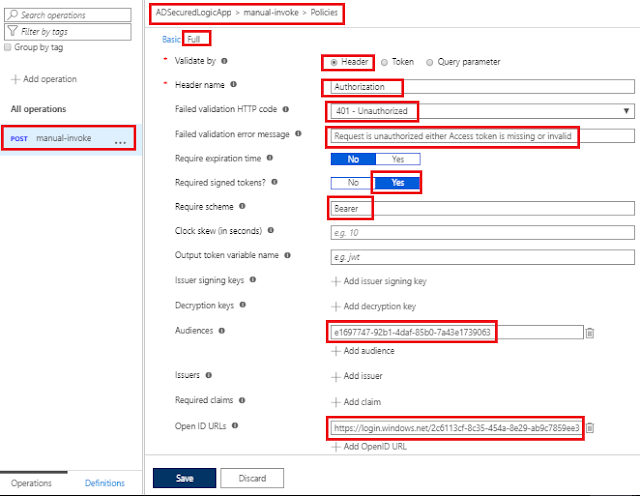
Configure Validate JWT Policy in Full mode
Validate by - As we are going to check header , set this to header.
Header name - name of header to be validated, set this to Authorization
Failed validation HTTP code - what HTTP error code you want to return when validation fails, set this to 401
Failed validation error message - what error messages you want to return when validation fails
Required signed tokens? - All Azure tokens are already digitally signed so it has no effect but,set it to Yes.
Require scheme - Which authorization scheme you want, set it to Bearer
Audiences - Against whom the token is to be validated, enter the Application ID of the AD app created in step 1
Open ID URLs - This is Authority which APIM will call internally to validate the received token, either of the below can be used
https://login.windows.net/<tenant_name>.onmicrosoft.com/.well-known/openid-configuration
https://login.windows.net/<tenant_id>/.well-known/openid-configuration
As logic app does not understands Authorization header , we need to remove it before forwarding request to Logic App and that can be done by using Set headers policy
Read - The request has both SAS authentication scheme and 'Bearer' authorization scheme. Only one scheme should be used
Configure Set Header Policy
Policies should look like
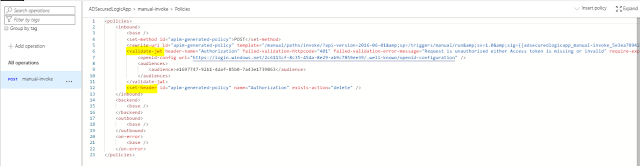
And in code view
That's it, the Logic App is now secured with Azure Active Directory by using Azure APIM. So if someone has to access the logic App it has to present Access token and make a call to the Url set in APIM
Testing
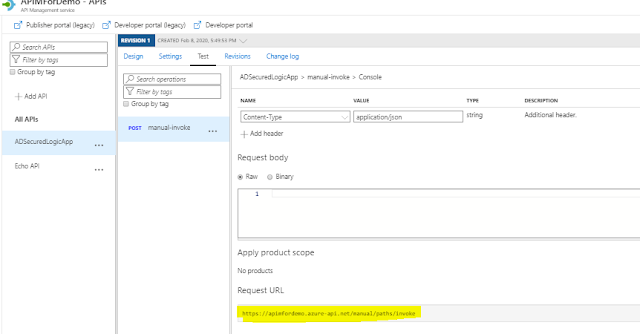
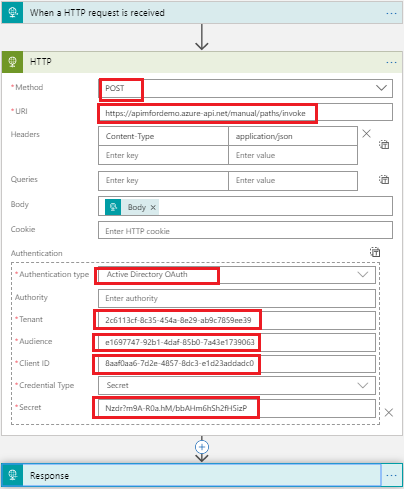
For testing it , have used another Logic App which will make call with access token to new URL.We need now the URL of API created in APIM (whose backend is Logic App), we can get it from Test tab as below.
Have covered detailed steps in following post for details - Calling Active Directory Secured Function App from Logic Apps
Using postman, did sent a request to above callerlogicapp and received a response
How it works
As logic app is imported in APIM, an API gets created with a new URL. When a caller/client sends a request along with the access token to this url, APIM applies the policies we have set on Inbound Processing section.
Using validate JWT token policy it cross verifies the presented token with Active directory internally (via the open ID URL) and Audience claim (against the configured audience id).
If all ok, next policies are executed (like Set header which removes Authorization header etc) and finally request forwarded to backend (logic app). Response is collected from it and sent back to the caller/client.
If token validation fails then caller/client will be sent error message - Request is unauthorized either Access token is missing or invalid
If you have questions or suggestions, feel free to do in comments section below !!!
Do share if you find this helpful .......
Knowledge Sharing is Caring !!!!!!
Learn More about Logic App
- How to configure Logic App Standard workflow behind Azure APIM
- How to Query Azure Table storage from Logic App | How to filter results of Azure Table storage from Logic App
- Understanding expressions in Logic Apps | Frequently used expressions in Logic Apps | What is expressions in Logic App
- How to use Logic app Run History | How to troubleshoot Logic App workflow execution
- Logic App and Slack - Sending messages to slack channel | Logic app and slack integration | Connecting Logic App to Slack channel
- How to access Application settings fields value from Logic app Standard workflow | Using Application settings as configuration store for Logic app standard workflow
- Developing Logic app standard workflow which uses Map locally and deploying to Azure
- Developing Logic App Standard Workflow Using Visual Studio Code | Create Logic App Standard Workflow Using Visual Studio Code
- Logic App - Xml to Json using Liquid Map | Append in Liquid Map
- How to use Azure Event Grid Custom Topic | Publishing and Subscribing from Azure Event Grid Custom Topic using Logic App
- Using Azure Storage Account Table as Config Store for Logic Apps | How to read and write from Logic App to Azure Storage Account Table
- Get Logic App Name in Logic App
- Difference between Logic App Consumption and Logic App Standard
- Getting Started with Logic App Standard | Overview of Logic App Standard | Basics of Logic App Standard
- How to find count of Logic App executions using Azure Portal
- Azure Functions vs Azure Logic App | Difference between Azure Functions and Azure Logic App
- Getting started with Logic App : Liquid Map | Using Liquid template in Logic app
- How to get actual error message of Scope in Logic App | Exception Handling in Logic app
- Interview questions and answers on Logic Apps | Interview questions for azure logic app developers
- How to execute Stored Procedure in Logic App | How to connect to SQL in Logic App
- How to get current date in logic app | How to format date time in Logic App
- BizTalk Developer getting started with Logic App
- Getting Started with Logic Apps - Fundamentals
- Getting Started with Logic Apps - Enterprise Application Integration
- Getting Started with Logic Apps - AS2
- Getting Started with Logic Apps - EDI X12 Fundamentals
- Getting Started with Logic Apps - XML to EDI X12
- Getting Started with Logic Apps - EDI X12 to XML
- Getting Started with Logic Apps - What happened to the Request?
- Inserting Multiple Records In On Prem SQL Using Logic App
- Inserting data in On Premises SQL Database using Logic Apps
- Installing and Configuring On Premises Data Gateway - By adding user to Active Directory
- XML Batching(Aggregation) in Logic App
- Batching(Aggregating) messages in Logic App
- Debatching(Splitting) JSON Message in Logic Apps - ForEach and SplitOn
- Debatching(Splitting) XML Message in Logic Apps - ForEach and SplitOn
- Securing Logic App with Azure Active Directory authentication
- Removing ns0: prefix from xml output from BizTalk/Logic app XSLT map
- Using Managed Identity in Logic Apps for Calling Active Directory Secured Function App
- Logic Apps : Fetching ISA and GS Segment Values From Interchange Envelope and Mapping
- Logic Apps : For Each Inside a For Each - Fetching values from field in an array inside an array
- How to configure Logic App Standard workflow behind Azure APIM
- How to Query Azure Table storage from Logic App | How to filter results of Azure Table storage from Logic App
- Understanding expressions in Logic Apps | Frequently used expressions in Logic Apps | What is expressions in Logic App
- How to use Logic app Run History | How to troubleshoot Logic App workflow execution
- Logic App and Slack - Sending messages to slack channel | Logic app and slack integration | Connecting Logic App to Slack channel
- How to access Application settings fields value from Logic app Standard workflow | Using Application settings as configuration store for Logic app standard workflow
- Developing Logic app standard workflow which uses Map locally and deploying to Azure
- Developing Logic App Standard Workflow Using Visual Studio Code | Create Logic App Standard Workflow Using Visual Studio Code
- Logic App - Xml to Json using Liquid Map | Append in Liquid Map
- How to use Azure Event Grid Custom Topic | Publishing and Subscribing from Azure Event Grid Custom Topic using Logic App
- Using Azure Storage Account Table as Config Store for Logic Apps | How to read and write from Logic App to Azure Storage Account Table
- Get Logic App Name in Logic App
- Difference between Logic App Consumption and Logic App Standard
- Getting Started with Logic App Standard | Overview of Logic App Standard | Basics of Logic App Standard
- How to find count of Logic App executions using Azure Portal
- Azure Functions vs Azure Logic App | Difference between Azure Functions and Azure Logic App
- Getting started with Logic App : Liquid Map | Using Liquid template in Logic app
- How to get actual error message of Scope in Logic App | Exception Handling in Logic app
- Interview questions and answers on Logic Apps | Interview questions for azure logic app developers
- How to execute Stored Procedure in Logic App | How to connect to SQL in Logic App
- How to get current date in logic app | How to format date time in Logic App
- BizTalk Developer getting started with Logic App
- Getting Started with Logic Apps - Fundamentals
- Getting Started with Logic Apps - Enterprise Application Integration
- Getting Started with Logic Apps - AS2
- Getting Started with Logic Apps - EDI X12 Fundamentals
- Getting Started with Logic Apps - XML to EDI X12
- Getting Started with Logic Apps - EDI X12 to XML
- Getting Started with Logic Apps - What happened to the Request?
- Inserting Multiple Records In On Prem SQL Using Logic App
- Inserting data in On Premises SQL Database using Logic Apps
- Installing and Configuring On Premises Data Gateway - By adding user to Active Directory
- XML Batching(Aggregation) in Logic App
- Batching(Aggregating) messages in Logic App
- Debatching(Splitting) JSON Message in Logic Apps - ForEach and SplitOn
- Debatching(Splitting) XML Message in Logic Apps - ForEach and SplitOn
- Securing Logic App with Azure Active Directory authentication
- Removing ns0: prefix from xml output from BizTalk/Logic app XSLT map
- Using Managed Identity in Logic Apps for Calling Active Directory Secured Function App
- Logic Apps : Fetching ISA and GS Segment Values From Interchange Envelope and Mapping
- Logic Apps : For Each Inside a For Each - Fetching values from field in an array inside an array







Nice Article! From where u are getting ClientID and Client Secret Values in HTTP connector- Securing Logic App with Azure Active Directory authentication
ReplyDeleteIt looks like they've added AAD OAuth authentication to logic app request triggers ... https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#enable-oauth
ReplyDeletewhere do we get client id used while testing?
ReplyDeleteExcellent article ... many thanks for sharing
ReplyDeleteOne point ... "not all Azure services support Azure AD authentication and Logic App is one of them"
Looks like AAD support has been added to logic apps ...
https://docs.microsoft.com/en-us/azure/logic-apps/logic-apps-securing-a-logic-app#enable-azure-active-directory-oauth
Any chance of an article on how to use it :-) (I'm struggling to understand it)
I keep trying to get this to work, but the test always returns the error HTTP/1.1 401 Unauthorized. Then in the trace I find:
ReplyDeleteOn error
(-0.145 ms)↑ Back to top
validate-jwt (-0.145 ms)
{
"message": "JWT Validation Failed: JWT not present.."
}
I don't know what I'm missing.