{tocify} $title={Table of Contents}
Tenant ID(Directory ID) -- It is the authority which grants the token
AudienceID - For whom the token will be created i.e.Target AD App's client ID
Client ID and Client Secret - It is caller AD app's details, this proves client identity
Thus other steps remains same, in order to call AD secured app you(client/calling app) need to get access token from AD and for doing that you need to prove your identity with AD.
Introduction
In last post we saw how to secure a Function App with Active directory and how to make call to it from another function App.
And for doing it from function we used libraries provided by Microsoft i.e., Microsoft.IdentityModel.Clients.ActiveDirectory;
So how do we do this in logic app? How do we add the above library to logic app and where do we write code? – No code required as Logic app already supports Active Directory OAuth out of box .
We just need to provide the following info
Tenant ID(Directory ID) -- It is the authority which grants the token
AudienceID - For whom the token will be created i.e.Target AD App's client ID
Client ID and Client Secret - It is caller AD app's details, this proves client identity
Thus other steps remains same, in order to call AD secured app you(client/calling app) need to get access token from AD and for doing that you need to prove your identity with AD.
And to create identity we need to register an App with AD. And then you use this identity to request access token.
So first we need to get access token, and to request token we need
Create a simple http triggered logic app which will get triggered upon receiving http request and then calls the secured function app and sends back response . In response it will add whatever received from secured function app.
and it returns result as "Reply from target app,+input it received"
Use any rest client and make call to logic app and pass on input in expected format as above and below is the result
How to do it
So first we need to get access token, and to request token we need
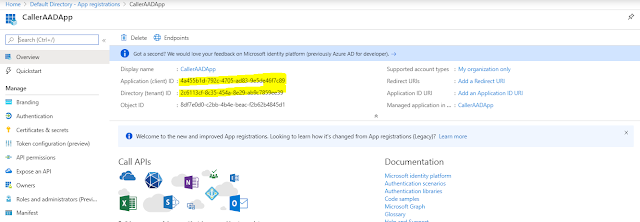
Register an Application with Active directory (Caller AD App)
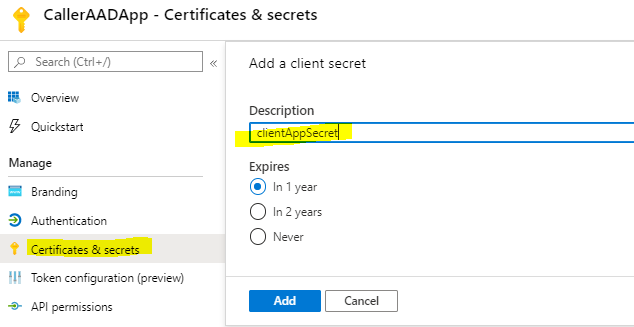
As this app will be used to get token, we need to make note of application(client) ID and also need to create a secret
Remember to copy and save the secret as it won't be visible later
Create Logic App
Create a simple http triggered logic app which will get triggered upon receiving http request and then calls the secured function app and sends back response . In response it will add whatever received from secured function app.
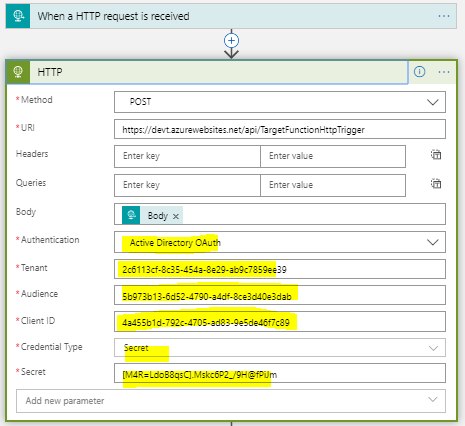
In second step note that we are using HTTP action rather than using Azure Functions action and it is because Azure Functions action does not support adding authentication details, whereas Http action is flexible with it.
After adding http action, Select POST as method and provide the url of secured function app. In Authentication select Active Directory OAuth and provide the other details as shown below
Here I personally think, having an application settings for logic Apps would be good to have feature. However we can use Key Vault here to store the info and fetch values at runtime but for the sake of post, have done it here itself.
 |
Now add http response action and against body - select the body returned from above step
|
That's it logic app is ready to use.
Testing
The target function expects input in following form
{"name":"Input"}
and it returns result as "Reply from target app,+input it received"
How it works
When calling from function app we had to explicitly call the endpoint (https://login.microsoftonline.com/) alongwith the details like TenantId, AudienceID, ClienID and Secret using the provided library, however in case of logic app you just need to configure the details and rest is taken care by http connector.
If you have questions or suggestions, feel free to do in comments section below !!!
Do share if you find this helpful .......
Knowledge Sharing is Caring !!!!!!
Learn More about Logic App
- How to configure Logic App Standard workflow behind Azure APIM
- How to Query Azure Table storage from Logic App | How to filter results of Azure Table storage from Logic App
- Understanding expressions in Logic Apps | Frequently used expressions in Logic Apps | What is expressions in Logic App
- How to use Logic app Run History | How to troubleshoot Logic App workflow execution
- Logic App and Slack - Sending messages to slack channel | Logic app and slack integration | Connecting Logic App to Slack channel
- How to access Application settings fields value from Logic app Standard workflow | Using Application settings as configuration store for Logic app standard workflow
- Developing Logic app standard workflow which uses Map locally and deploying to Azure
- Developing Logic App Standard Workflow Using Visual Studio Code | Create Logic App Standard Workflow Using Visual Studio Code
- Logic App - Xml to Json using Liquid Map | Append in Liquid Map
- How to use Azure Event Grid Custom Topic | Publishing and Subscribing from Azure Event Grid Custom Topic using Logic App
- Using Azure Storage Account Table as Config Store for Logic Apps | How to read and write from Logic App to Azure Storage Account Table
- Get Logic App Name in Logic App
- Difference between Logic App Consumption and Logic App Standard
- Getting Started with Logic App Standard | Overview of Logic App Standard | Basics of Logic App Standard
- How to find count of Logic App executions using Azure Portal
- Azure Functions vs Azure Logic App | Difference between Azure Functions and Azure Logic App
- Getting started with Logic App : Liquid Map | Using Liquid template in Logic app
- How to get actual error message of Scope in Logic App | Exception Handling in Logic app
- Interview questions and answers on Logic Apps | Interview questions for azure logic app developers
- How to execute Stored Procedure in Logic App | How to connect to SQL in Logic App
- How to get current date in logic app | How to format date time in Logic App
- BizTalk Developer getting started with Logic App
- Getting Started with Logic Apps - Fundamentals
- Getting Started with Logic Apps - Enterprise Application Integration
- Getting Started with Logic Apps - AS2
- Getting Started with Logic Apps - EDI X12 Fundamentals
- Getting Started with Logic Apps - XML to EDI X12
- Getting Started with Logic Apps - EDI X12 to XML
- Getting Started with Logic Apps - What happened to the Request?
- Inserting Multiple Records In On Prem SQL Using Logic App
- Inserting data in On Premises SQL Database using Logic Apps
- Installing and Configuring On Premises Data Gateway - By adding user to Active Directory
- XML Batching(Aggregation) in Logic App
- Batching(Aggregating) messages in Logic App
- Debatching(Splitting) JSON Message in Logic Apps - ForEach and SplitOn
- Debatching(Splitting) XML Message in Logic Apps - ForEach and SplitOn
- Securing Logic App with Azure Active Directory authentication
- Removing ns0: prefix from xml output from BizTalk/Logic app XSLT map
- Using Managed Identity in Logic Apps for Calling Active Directory Secured Function App
- Logic Apps : Fetching ISA and GS Segment Values From Interchange Envelope and Mapping
- Logic Apps : For Each Inside a For Each - Fetching values from field in an array inside an array