{tocify} $title={Table of Contents}
But I had created the connection
Error/Issue:
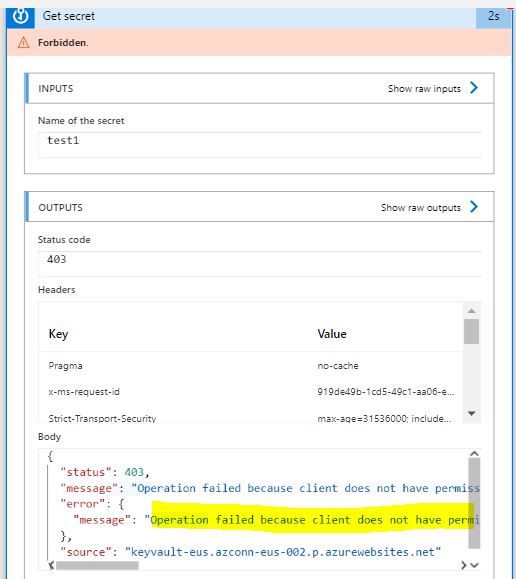
While trying to Get Secret from Key vault, following error was presented
"Operation failed because client does not have permission to perform the operation on the key vault. Please check your permissions in the key vault access policies"
Why it happened
As the error says, client does not have permission to perform the operation on the key vault. Please check your permissions in the key vault access policies - thus just creating a connection to Keyvault does not give you the permission .
When connection is created only Authentication happens but to access the Key Vault artifacts Authorization is to be done.
And you authorize by adding the service principal of an Identiy in an Access policy of Keyvault along with selecting what all actions can be performed.
What to do
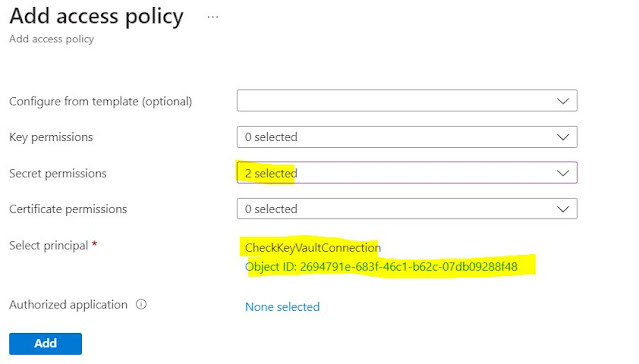
Click on Access policies section, select Permission model as Vault access policy and click on Add Access Policy
Added the logic app service principal in Access Policy of KeyVault.
Permissions should be selected as per the need and as I needed to see the list of secrets and get the value of secret - selected both as can be seen in below image.
Did save and the issue was gone.
If you have questions or suggestions, feel free to do in comments section below !!!
Do share if you find this helpful .......
Knowledge Sharing is Caring !!!!!!
Related Post
- Getting Started with Logic Apps - Enterprise Application Integration
- Getting Started with Logic Apps - EDI X12 Fundamentals
- Getting Started with Logic Apps - Fundamentals
- Getting Started with Logic Apps - AS2
- Getting Started with Logic Apps - XML to EDI X12
Tags:
Azure Key Vault error


Hi Can you elaborate on the "Added the logic app service principal in Access Policy of KeyVault." point.
ReplyDeleteI am facing this error when I try to use key vault connector from Power Automate.
Steps are same for Logic App and Power Automate
ReplyDeleteTo add a Power Automate identity to Key Vault access, you need to create a managed identity for Power Automate and then assign the managed identity to a Key Vault role.
To create a managed identity for Power Automate, follow these steps:
Sign in to the Azure portal.
Navigate to the Power Automate service.
Select your environment from the top-right corner.
Select Settings (gear icon) > View all Power Automate settings.
Under Security, select Identity.
Set Enable managed identity to On.
Select Save.
Once you have created a managed identity for Power Automate, you need to assign the managed identity to a Key Vault role. To do this, follow these steps:
Sign in to the Azure portal.
Navigate to your Key Vault.
Select Access policies.
Select Add access policy.
Under Select principal, select Managed identity and then select the Power Automate managed identity.
Under Select role, select the Key Vault role that you want to assign to the managed identity.
Select Save.
Once you have assigned the Power Automate managed identity to a Key Vault role, the Power Automate service will be able to access the Key Vault resources that are assigned to that role.
ReplyDeleteTo add a Power Automate identity to Key Vault access, you need to create a managed identity for Power Automate and then assign the managed identity to a Key Vault role.
To create a managed identity for Power Automate, follow these steps:
Sign in to the Azure portal.
Navigate to the Power Automate service.
Select your environment from the top-right corner.
Select Settings (gear icon) > View all Power Automate settings.
Under Security, select Identity.
Set Enable managed identity to On.
Select Save.
Once you have created a managed identity for Power Automate, you need to assign the managed identity to a Key Vault role. To do this, follow these steps:
Sign in to the Azure portal.
Navigate to your Key Vault.
Select Access policies.
Select Add access policy.
Under Select principal, select Managed identity and then select the Power Automate managed identity.
Under Select role, select the Key Vault role that you want to assign to the managed identity.
Select Save.
Once you have assigned the Power Automate managed identity to a Key Vault role, the Power Automate service will be able to access the Key Vault resources that are assigned to that role.